Proxy Design Pattern
What is Proxy Design Pattern?
- Proxy – “in place of” or “representing” or “on behalf of”.
- Proxy is the object that is being called by the client to access the real object behind the scene.
- A proxy is a placeholder for another object to control the access.
- The proxy pattern represents the functionality of another class.
- Virtual proxy is a placeholder for “expensive to create” objects. The real object is only created when a client requests/access the object.
- The remote proxy provides a local representative for an object that resides in a different address space.
- Protective proxy controls access to a sensitive master object. It checks whether the caller has permission and etc.
Table of Contents
Real Life Examples of Proxy Design Pattern
Let's consider a person named John. He's trying to get 500 Rupees from his account. He has an account in XYZ bank. He would have two options to withdraw 500 rupees from brown.
First Approach:
The first approach is visiting the bank. In the first approach, what he would do is, he would try to visit the bank then he would fill the challan, withdraw challan and he will try to show that  withdraw challan to the cashier and that cashier would check the credentials whether the account is valid or not and whether the sufficient funds are present or not. After that, the cashier would return 500 Rs to John. Here, John is spending money as well as time for withdrawing 500 Rs.
withdraw challan to the cashier and that cashier would check the credentials whether the account is valid or not and whether the sufficient funds are present or not. After that, the cashier would return 500 Rs to John. Here, John is spending money as well as time for withdrawing 500 Rs.
Consider John is residing at a location A. Bank is residing at location B. The distance between A and B is five kilometers. To cover this distance, John is traveling by bike. So, for that, he needs to spend some amount on petrol and also the time. So, to move five kilometers, it would take some time. Thus, by using the first approach, John is spending both money and time for withdrawing 500 Rs.
Second Approach:
There’s a second approach where John visits the nearest ATM, and then he uses the bank debit card and enters the required credentials like PIN and other stuff, and then he withdraws the money. Here, that ATM will act as a proxy object. It will try to communicate with the real object, and it will check whether that account has sufficient funds and then it will check the other credentials. Then, the real object communicates with the proxy object regarding the status.
Here, that ATM will act as a proxy object. It will try to communicate with the real object, and it will check whether that account has sufficient funds and then it will check the other credentials. Then, the real object communicates with the proxy object regarding the status.
Here, the proxy object is playing a significant role behind the scene. This proxy object is handling the request on behalf of us. So, by following the second approach, John is saving both time and money because nowadays ATM is present in every street. So, he could save both money and time to withdraw 500 Rs.
Proxy Design Pattern Technical Example
Let’s consider there are two objects. So, there’s a real object which is the placeholder for another object to control the access.
Proxy object will try to control the access to the real object.
Let’s suppose a client is trying to access the real object, proxy object will come into an act, and it will try to check whether the client has the permission to access the real object.
Here, the Proxy is the object that is being called by the client to access the real object behind the scene.
The client knows only the proxy object. The client isn’t aware of the real object. The proxy object will try to manage those internal things, and it will try to contact the real object and get the relevant information. The proxy object will serve the client.
Proxy Design Pattern Technical Example
Virtual Proxy
For example, Let’s suppose if your client is trying to access the student data of a particular student. The client is accessing the “Student ID 1” data.
Here, the client doesn’t have access to the real object. The client has access only to the proxy object. The client knows that there are objects that will be served for the request. The client knows the real object won’t be created until the client requests the actual thing. Till that time this proxy would be shown to the client.
When the client sends a request then only that the Server would create real object. For example, “Student ID 1” is the actual request submitted during the runtime, and that actual data would be converted to the real object. That real object would be served to the client. So this is the procedure for the Proxy Design Pattern, Virtual proxy.
In software applications also, we are following Proxy Design Pattern for some use cases. So, you need , and you need to check whether that use case could fit in the Proxy Design Pattern or not.
Remote Proxy
The remote proxy provides a local representative for an object that resides in different address spaces.
For example, Let’s suppose if the actual data is present at various spaces. The client is unaware of those things. The client knows there would be some object that would be served when it triggers a request.
So here the proxy object would handle those things. The proxy object would get the object from the better address place for the particular request.
Protective Proxy
Protected proxy controls access to the sensitive master object. Let’s suppose if you’re studying in a college, you would have some lab sessions, and during those labs sessions, you can access the internet.
Let’s suppose if you’re trying to access social websites like Facebook, WhatsApp, etc. using college internet network. Then there will be some proxy server, which won’t allow you to access the Facebook server or WhatsApp server.
Here, this is acting as a Protective proxy. It is protecting the actual request based on the various criteria.
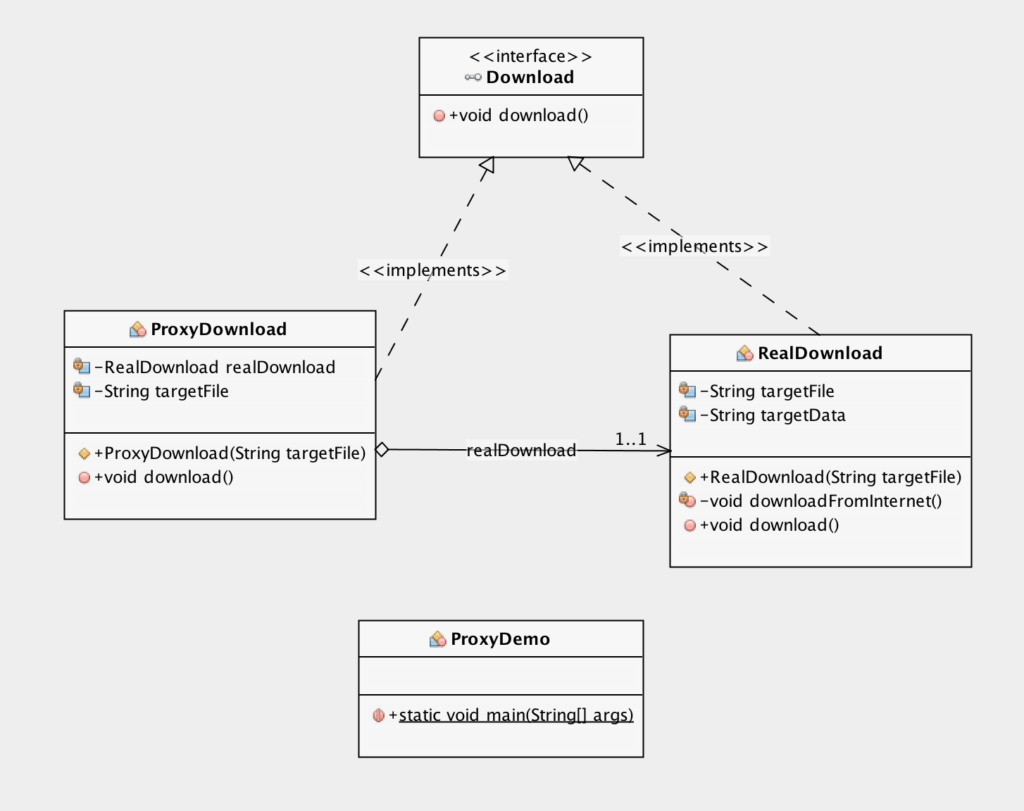
UML Class Diagram of Proxy Design Pattern
Proxy Design Pattern Java Implementation
Step 1:
- Create an interface Download with the abstract method download().
- In the Download interface, there is only one abstract method called void download().
- There are two implementation classes RealDownload and the ProxyDownload.
public interface Download
{
public void download();
}
Step 2:
- Create a class RealDownload which implements Download interface.
- RealDownload downloads the required target file from the internet and it will store it in the variable.
- The RealDownload which implements the Download interface and it has two local class variables called targetField and targetData.
- The targetField is the file that needs to be downloaded from internet. The targetData is the downloaded data of the targetFile.
- We need to specify the targetFile that needs to be downloaded. This method is called downloadFromInternet().
- If we look at the downloadFromInternet(), the target data that is getting assigned. Since it implements a Download interface. We need to Override the download() method.
- When we override the download() method System.out.println(this.targetData), we print the downloaded data
public class RealDownload implements Download
{
private String targetFile;
private String targetData;
public RealDownload(String targetFile)
{
this.targetFile = targetFile;
downloadFromInternet();
}
private void downloadFromInternet()
{
this.targetData="This is a test data ";
}
@Override
public void download()
{
System.out.println(this.targetData);
}
}
Step 3:
- Create a class ProxyDownload which implements Download Interface.
- This is the second implementing class implements Download interface which is ProxyDownload.
- Suppose if anyone calls this download method then we will try to create the RealDownload object.
- If RealDownload =new RealDownload(targetFile) then we will try to create the RealDownload object using the targetFile.
- For the second, third, fourth and the next successive times, we are not trying to create the RealDownload object because it will check whether it’s null. This stage can be skipped, try to retain the local copy data. This is the concept behind the use of Proxy Design Pattern.
public class ProxyDownload implements Download
{
private RealDownload realDownload;
private String targetFile;
public ProxyDownload(String targetFile)
{
this.targetFile=targetFile;
}
@Override
public void download()
{
if(realDownload==null)
{
realDownload=new RealDownload(targetFile);
}
realDownload.download();
}
}
Step 4:
- Create a class ProxyDemo which is the class that handles everything.
- We will try to create the object for proxy download class. The download xyz.movie is the target file, and then we print the data and download.
- For the first time, the RealDownload object would be created. For the next successive method invitation this RealDownload object will not be created, it will return the locally copied data.
public class ProxyDemo
{
public static void main(String[] args)
{
Download download=new ProxyDownload("xyz.movie");
download.download();
System.out.println("");
download.download();
}
}

